
Individual crouching with shield intercepting DDOS-labeled missiles targeting an abstract object. Ideal for cybersecurity, data protection, defense, internet security, threat mitigation, digital

Cybersecurity in cloud-based media management. Protecting data files and documents in digital folders during data transfers. Vector illustration of cloud storage icon.

Robot holding a shield faces an expanding cone, symbolizing protection. Checkmark emphasizes security, trust, and safety. Ideal for cybersecurity, defense, AI protection, trust assurance risk

Cyber security risk management abstract concept vector illustration. Cyber security report analysis, risk mitigation management, protection strategy, identify digital threat abstract metaphor.

Cyber security risk Cyber security report analysis, risk mitigation management, protection strategy, identify digital threat Flat vector Modern illustration

Cyber security risk management abstract concept vector illustration. Cyber security report analysis, risk mitigation management, protection strategy, identify digital threat abstract metaphor.

Cyber security risk management abstract concept vector illustration. Cyber security report analysis, risk mitigation management, protection strategy, identify digital threat abstract metaphor.

Cyber security risk management abstract concept vector illustration. Cyber security report analysis, risk mitigation management, protection strategy, identify digital threat abstract metaphor.

Cybersecurity, web safety, digital defense futuristic concept with protection shield and power button in glowing low polygonal style on dark blue background. Modern abstract design vector illustration

Cyber security risk management abstract concept vector illustration. Cyber security report analysis, risk mitigation management, protection strategy, identify digital threat abstract metaphor.

Cyber security risk management abstract concept vector illustration. Cyber security report analysis, risk mitigation management, protection strategy, identify digital threat abstract metaphor.

Cyber security risk management abstract concept vector illustration. Cyber security report analysis, risk mitigation management, protection strategy, identify digital threat abstract metaphor.

Cyber security risk management abstract concept vector illustration. Cyber security report analysis, risk mitigation management, protection strategy, identify digital threat abstract metaphor.

Set of 27 outline web crisis management icons such as security, family insurance, solution, recovery, assembly point, press conference, compliance, warning vector thin line icons for web design,

Crisis word cloud concept. Vector illustration

Emergency word cloud concept. Vector illustration

Emergency word cloud concept. Vector illustration

Crisis word vector, creative banner.

Crisis word cloud concept. Vector illustration

Emergency word cloud collage, healthcare concept background

Emergency word cloud collage, healthcare concept background

Set of Different Shields for Security Concept

Young character escaping from the office reduction, HR, scared manager haunted by huge scissors

Emergency mind map, concept for presentations and report

Risk meter indicating low risk level with colorful speedometer and gauge

Risk Management, vector, pixel perfect, illustrator file

Zero-day Exploit, vector, pixel perfect, illustrator file

Incident Response, vector, pixel perfect, illustrator file

Awareness Hub, vector, pixel perfect, illustrator file

Cyber Resilience, vector, pixel perfect, illustrator file

Brute Force Protection, vector, pixel perfect, illustrator file

Risk Assessment, vector, pixel perfect, illustrator file

Incident Response, vector, pixel perfect, illustrator file

Cyber Deception, vector, pixel perfect, illustrator file

Ddos Attack, vector, pixel perfect, illustrator file

Awareness Booster, vector, pixel perfect, illustrator file

Brute Force Protection, vector, pixel perfect, illustrator file

Brute Force Protection, vector, pixel perfect, illustrator file

Web Application Firewall, vector, pixel perfect, illustrator file

Ddos Attack, vector, pixel perfect, illustrator file

Botnet Detection, vector, pixel perfect, illustrator file

Cyber Resilience, vector, pixel perfect, illustrator file

Risk Assessment, vector, pixel perfect, illustrator file

Botnet Detection, vector, pixel perfect, illustrator file

Awareness Booster, vector, pixel perfect, illustrator file

Rockets labeled DDoS moving toward a shielding hand, indicating protection against cyberattacks. Cloud element symbolizes internet. Ideal for cybersecurity, protection, hacking, data, safety

Man deflects cyberattacks with shield, woman adjusts settings for protection. Ideal for cybersecurity, IT defense, data security, system controls, cloud safety, risk management, simple flat metaphor

Cyber Deception, vector, pixel perfect, illustrator file

Web Application Firewall, vector, pixel perfect, illustrator file

Zero-day Exploit, vector, pixel perfect, illustrator file

Awareness Hub, vector, pixel perfect, illustrator file

Threat Hunting, vector, pixel perfect, illustrator file

Cyber Deception, vector, pixel perfect, illustrator file

Brute Force Protection, vector, pixel perfect, illustrator file

Risk Assessment, vector, pixel perfect, illustrator file

Cyber Deception, vector, pixel perfect, illustrator file

Awareness Booster, vector, pixel perfect, illustrator file

Web Application Firewall, vector, pixel perfect, illustrator file

Zero-day Exploit, vector, pixel perfect, illustrator file

Person wielding shield blocking DDOS missiles, magnifying glass symbolizing analysis, thumbs-up for security approval. Ideal for cybersecurity, protection, risk management, threat detection, IT

Team protecting systems from DDoS threats using shield, coding support, and analyzing performance charts. Ideal for security, teamwork, problem-solving, resilience, IT, technology simple landing

Risk Management, vector, pixel perfect, illustrator file

Zero-day Exploit, vector, pixel perfect, illustrator file

Botnet Detection, vector, pixel perfect, illustrator file

Risk Assessment, vector, pixel perfect, illustrator file

Incident Response, vector, pixel perfect, illustrator file

Web Application Firewall, vector, pixel perfect, illustrator file

Zero-day Exploit, vector, pixel perfect, illustrator file

Ddos Attack, vector, pixel perfect, illustrator file

Cloud with lock symbolizing data protection, bug icon denoting cybersecurity threats, and factory emitting pollution. Ideal for cybersecurity, cloud computing, data privacy, threat management

Risk Management icon sheet multiple style collection

Risk Management, vector, pixel perfect, illustrator file

Brute Force Protection, vector, pixel perfect, illustrator file

Risk Assessment, vector, pixel perfect, illustrator file

Awareness Hub, vector, pixel perfect, illustrator file

Risk Assessment, vector, pixel perfect, illustrator file

Cyber Deception, vector, pixel perfect, illustrator file

Brute Force Protection, vector, pixel perfect, illustrator file

Awareness Hub, vector, pixel perfect, illustrator file

Web Application Firewall, vector, pixel perfect, illustrator file

Awareness Booster, vector, pixel perfect, illustrator file

Ddos Attack, vector, pixel perfect, illustrator file

Evacuation types yellow onboarding template. Building evacuation. Responsive mobile website with linear concept icons. Web page walkthrough 4 step screens. Lato-Bold, Regular fonts used

Emergency word cloud concept. Vector illustration

Magnifier next to a digital shield and cloud emphasizing data protection, security, and analysis. Ideal for cybersecurity, privacy, cloud computing, technology, data analysis, secure storage

Lock symbolizing security, skull for threat, VPN shield for online safety, and stacked coins for digital assets. Ideal for cybersecurity, data privacy, encryption, online safety, financial security

Risk Management, vector, pixel perfect, illustrator file

Risk Management, vector, pixel perfect, illustrator file

Scissors cutting URL symbolize threat blocking, shield represents data security, icons for information, geolocation. Ideal for cybersecurity, privacy, risk management, software, technology data

Cyber Deception, vector, pixel perfect, illustrator file

Awareness Booster, vector, pixel perfect, illustrator file

Ddos Attack, vector, pixel perfect, illustrator file

Cyber Deception, vector, pixel perfect, illustrator file

Zero-day Exploit, vector, pixel perfect, illustrator file

Cyber Resilience, vector, pixel perfect, illustrator file

Awareness Booster, vector, pixel perfect, illustrator file

Risk Assessment, vector, pixel perfect, illustrator file

Zero-day Exploit, vector, pixel perfect, illustrator file
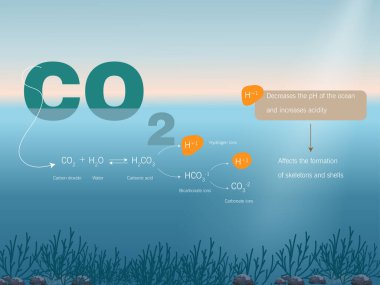
Ocean acidification process.chemical equation and consequences

Risk mitigation, identify threat and control or prevent potential impact, reduce chance of failure, uncertainty, evaluate safety level, businessman with protection umbrella on risk gauge measuring.