
Risk management asset vulnerability assessment concept vector

Risk management asset vulnerability assessment concept vector

Cybersecurity protects digital systems, networks, and data from cyber threats, hacking, and unauthorized access. It ensures online safety, data privacy, and secure communication through encryption, firewalls, and advanced security protocols.

Cybersecurity system, hosting on server, accepted secure wireless connection global GPS, data update protection with shield. Online security trendy red black thin line icons set vector illustration.

Manual tester and automated software tester bug to do QA testing to test software

Penetration Testing or pen test to analyze a potential cyber attack and its potential vulnerabilities for database

Bug bounty program is a deal offered for hackers or developers to receive compensation for reporting bugs, security exploits and vulnerabilities

Bug bounty program is an offer for hackers or developers to receive compensation for reporting bugs, security exploits and vulnerabilities

Bug bounty program is an offer for hackers or developers to receive compensation for reporting bugs, security exploits and vulnerabilities

Digital security and global network shown via stylized, modern vector icons.

Penetration Testing stages to better understand how a potential cyber attack and its potential vulnerabilities for security

Ultimate collection of 24 vector icons representing Threat in Flat aesthetic, optimized with 128x128 PIXEL perfect resolution for maximum impact.

Precision-engineered 24 LineFill vector icons for Risk, designed at 128x128 PIXEL perfect resolution for exceptional clarity and scalability.

Set of Different Shields for Security Concept

The image showcases a black outline icon of a padlock against a pristine white backdrop, ideal for security, protection, privacy, and secure access concepts.

Software penetration testing types circular diagram infographic. Debugging methodology. Data visualization with 3 options. Hierarchy chart round. Montserrat SemiBold, Lato Regular fonts used

Artfully designed 32 Thin Line PIXEL perfect vector icons for Security, delivered in 128x128 format for consistent visual excellence.

Protection shield with gear flat icon, vector, illustration, vulnerability assessment concept

Bug in coding software that need to do QA or software testing to find it
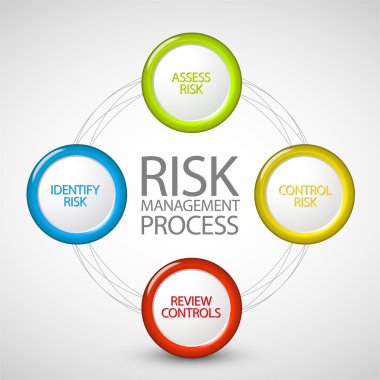
Vector Risk management process diagram schema
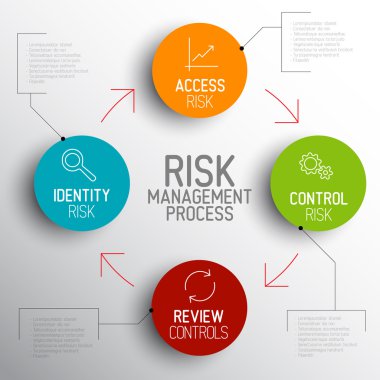
Vector light Risk management process diagram schema with description

Risk management process diagram, vector illustration
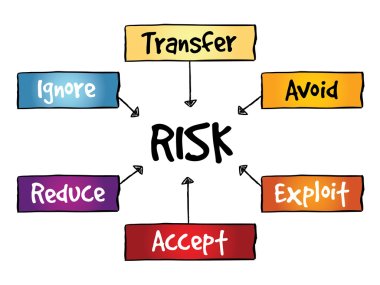
Risk management flow chart, business concept

Ethical hacking involves protection, security, and trust. Key objects, shield, lock, handshake. Outline icons set.

Risk management business calculation team work together on desk vector illustration vector illustration

Thin assess like review audit risk icon, symbol of find internal vulnerable bill or data research and survey concept linear trend quality logotype graphic art design

Risk management process, business concept

Risk management mind map flowchart business concept for presentations and reports

Crisis management process mind map, business concept

Risk management mind map flowchart business concept for presentations and reports

Vector Risk management process diagram schema

Risk management as possible profit and danger evaluation tiny person concept. Finance or earnings collection risk and future financial benefits assessment vector illustration. Business strategy path.

Cybersecurity dictionary and network security terms outline hands concept. Study online threats meaning to understand hacker attack types and possible computer vulnerability vector illustration.

Risk meter indicating low risk level with colorful speedometer and gauge

Security Policy, vector, pixel perfect, illustrator file

Data Insight Engine, vector, pixel perfect, illustrator file

Security Compliance, vector, pixel perfect, illustrator file

Framework Model, vector, pixel perfect, illustrator file

Awareness Hub, vector, pixel perfect, illustrator file

Shield With Checkmark, vector, pixel perfect, illustrator file

Security Policy, vector, pixel perfect, illustrator file

Posture Evaluation, vector, pixel perfect, illustrator file

Compliance Check, vector, pixel perfect, illustrator file

Data Insight Engine, vector, pixel perfect, illustrator file

Shield With Checkmark, vector, pixel perfect, illustrator file

Governance Control, vector, pixel perfect, illustrator file

Posture Scanner, vector, pixel perfect, illustrator file

Security Certification, vector, pixel perfect, illustrator file

Risk Assessment, vector, pixel perfect, illustrator file

Cybersecurity Audit, vector, pixel perfect, illustrator file

Cyber Risk Review, vector, pixel perfect, illustrator file

Training Simulator, vector, pixel perfect, illustrator file

Maturity Assessment, vector, pixel perfect, illustrator file

Policy Enforcement, vector, pixel perfect, illustrator file

Shield With Checkmark, vector, pixel perfect, illustrator file

Security Policy, vector, pixel perfect, illustrator file

Cyber Risk Review, vector, pixel perfect, illustrator file

Governance Control, vector, pixel perfect, illustrator file

Framework Model, vector, pixel perfect, illustrator file

Security Audit, vector, pixel perfect, illustrator file

Security Policy, vector, pixel perfect, illustrator file

Strategic Security Plan, vector, pixel perfect, illustrator file

Risk Management, vector, pixel perfect, illustrator file

Business Risk Assessment, vector, pixel perfect, illustrator file

Business Risk Assessment, vector, pixel perfect, illustrator file

3d blue magnifying glass with a shield icon inside Security, protection, safety, defense, risk assessment, quality control, cybersecurity concept. Low poly digital futuristic style, wireframe. Vector.

This collection features 32 Thin Outline PIXEL perfect vector icons tailored to the Security theme, optimized in 128x128 format for digital design.

Premium collection of 16 Thin Line vector icons for Security Breach, meticulously crafted in 128x128 PIXEL perfect resolution for superior visual impact.

Security Audit, vector, pixel perfect, illustrator file

Security Penetration, vector, pixel perfect, illustrator file

Security Certification, vector, pixel perfect, illustrator file

Security Penetration, vector, pixel perfect, illustrator file

Strategic Security Plan, vector, pixel perfect, illustrator file

Maturity Assessment, vector, pixel perfect, illustrator file

Security Blueprint, vector, pixel perfect, illustrator file

Shield With Checkmark, vector, pixel perfect, illustrator file

Policy Enforcement, vector, pixel perfect, illustrator file

Risk Assessment, vector, pixel perfect, illustrator file

Penetration Testing, vector, pixel perfect, illustrator file

Validation Layer, vector, pixel perfect, illustrator file

Cybersecurity Verification, vector, pixel perfect, illustrator file

Governance Control, vector, pixel perfect, illustrator file

Security Penetration, vector, pixel perfect, illustrator file

Security Blueprint, vector, pixel perfect, illustrator file

Posture Scanner, vector, pixel perfect, illustrator file

Maturity Matrix, vector, pixel perfect, illustrator file

Policy Enforcement, vector, pixel perfect, illustrator file

3d blue shield under a magnifying glass. Security, protection, safety, defense, risk assessment, quality control, cybersecurity concept. Low poly digital futuristic style, wireframe structure. Vector.

Handcrafted collection featuring 36 Flat Lineal Color vector icons for Risk, optimized in 128x128 PIXEL perfect resolution for premium digital experiences.

Robot holding shield with binary code, large gear, sad face. Ideal for technology, cybersecurity, automation, problem resolution, risk assessment AI ethics digital safety. Simple flat metaphor

Set line icons of risk management isolated on white. Big data, finance report, business strategy, binoculars, scales, chess, comparison, investment assessment. Vector illustration

Network management RGB color icons set. System architecture, digital administration. Performance monitoring. Isolated vector illustrations. Simple filled line drawings collection. Editable stroke

Cybersecurity Audit, vector, pixel perfect, illustrator file

Security Policy, vector, pixel perfect, illustrator file

Data Insight Engine, vector, pixel perfect, illustrator file

Security Penetration, vector, pixel perfect, illustrator file

Awareness Hub, vector, pixel perfect, illustrator file

Benchmark Standards, vector, pixel perfect, illustrator file

Security Policy, vector, pixel perfect, illustrator file

Shield With Checkmark, vector, pixel perfect, illustrator file